Connecting to Your PBX: Network Configuration
The following options are available to connect to a Daktela Cloud PBX:
Types of communication with a virtual PBX
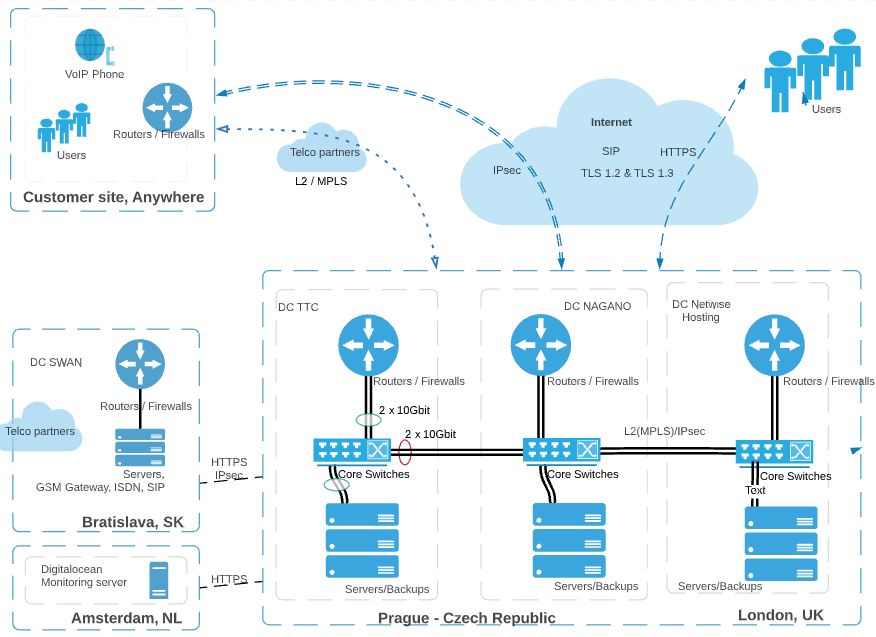
Connecting via the Internet
Basic connection type suitable for the vast majority of customers
PBX access via an address in the format customer.daktela.com
Communication with the PBX is protected using the HTTPS protocol during transfer
security recommendation: limiting communication only from customer IP addresses – typically the public addresses of the customer’s offices
VPN Using an IPsec Tunnel
This method is suitable for medium to large enterprises. The advantage of using the IPsec protocol is its security and isolation, allowing the PBX to become a secure part of the customer’s infrastructure.
We provide our customers that want to use this method with an IPsec concentrator (gateway). It is a fully scalable and redundant system built on the Router OS system.
The customer’s IT Specialist must collaborate with a Daktela Infrastructure Specialist to set up the IPsec tunnel. There is a configuration charge of 1 MD.
IP sec configuration parameters:
IKEv2 Policy-based:
IPsec gateway: 88.208.74.172
Phase 1 (IKEv2):
Encryption algorithm: aes-256-cbc
Hash alorithm: sha-384
DH group: DHGroup20 (ecp384)
Lifetime (seconds): 28800
Phase 2 (IPsec):
Encryption algorithm: aes-256-gcm (Preferred) / aes-256-cbc (Alternative)
Hash alorithm: null (Preferred) / sha-512 (Alternative)
PFS Group: DHGroup20 (ecp384)
Lifetime (seconds): 3600
Private Line – L2 Connection
A private line using the second network layer is a solution perfect for large companies. It eliminates many of the possible issues with throughput and security.
It is currently possible to set up an L2 connection to Daktela infrastructure in the following data centres:
TTC DC1, Tiskařská 257/10, 108 00 Praha 10, Czech Republic
DC Nagano, U nákladového nádraží 3153/8, 13000 Praha 3, Czech Republic
DC Netwise Netwise House, 24 Old Jamaica Road, London SE16 4AW, UK
Benestra HC, Údernícka 15, 851 01 Bratislava, Slovakia
Specifications and Responsibilities
Daktela suggests a preferred range from private address ranges for connecting network customers. This scope must be confirmed by both parties. In the event of a subsequent change request from the customer, this request must be confirmed again by Daktela. The range (subnet) 10.10.0.0/20, which is intended for internal use, is excluded from the given menu.
The customer sets up their L2 connection. Daktela can set it up on the customer’s behalf – talk to your account manager. Additional fees apply.
The service provider usually charges a fee.
Network devices (routers/firewalls) the customer wants to install in Daktela data centres have an element height limit of 1U on the rack.
Monitoring, configuration and management of L2 devices in Daktela data centers is the customer’s responsibility. Daktela currently provides only ICMP monitoring.
Only authorised persons from Daktela can physically access customer devices (routers/firewalls) in Daktela data centres. Customers do not have physical access.
Daktela supports BGP routing for L2 connections.
Daktela creates a separate and dedicated VLAN for each customer.
Using NAT on the customer’s L2 device is possible and recommended.
The customer’s IT Specialist must collaborate with a Daktela Infrastructure Specialist to set up the L2 connection. There is a configuration charge of 1 MD for service setup and connection of the L2 terminal equipment.
